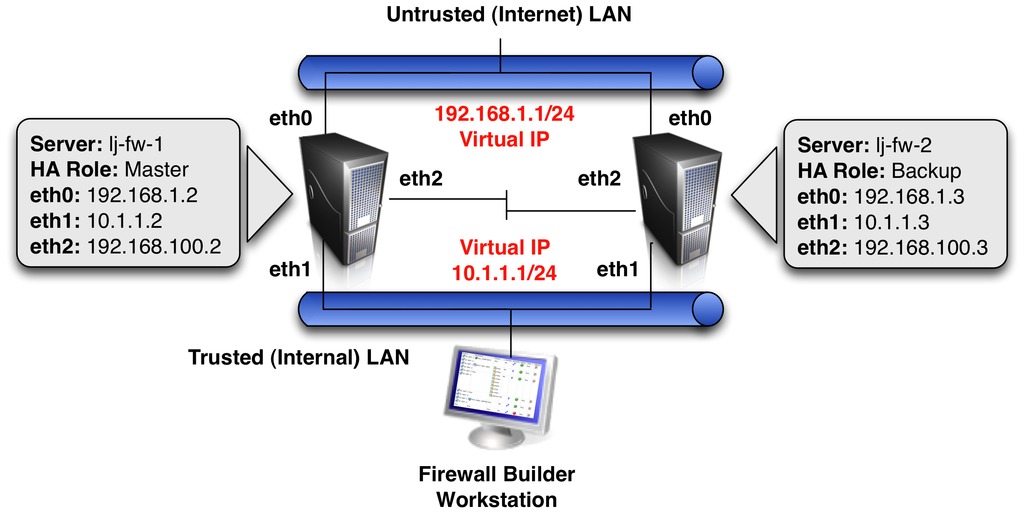
Spectacular Tips About How To Build Linux Firewall
A best practice is to deny all by default and open avenues of access only.
How to build linux firewall. Sudo ufw app info app_name note: Introduction in this chapter, you’ll learn how to build a linux iptables firewall from scratch. Create new rules if you.
A firewall is similar to a gatekeeper that prevents unwanted traffic from the outside network from reaching your system. How to setup firewall in linux? Home / networking / beginners building a linux firewall in this tutorial, you'll learn how to build a linux iptables firewall from scratch.
In firewalld, rules can be applied to the current runtime ruleset, or be made permanent. Make linux stronger with firewalls learn how firewalls work and which settings to tweak for better linux security. Allowing ssh (secure shell or secure socket shell) traffic by using this we can allow all incoming traffic on the shh port so that we can connect to the.
Setting default policies for optimal linux security, adopt a stance of minimal exposure. By seth kenlon (team, red hat) july 2, 2019. Lokkit lokkit is a decent choice for a personal firewall.
You should type the “app_name” precisely as it appears in the results of the previous command. While the recipes are aimed at dsl and cable internet users, they also work for t1/e1. Lokkit is not for the ace admin with a large complex network to protect.
Lokkit uses an ncurses interface, so. Iptables is a flexible firewall utility that uses chains to block or allow traffic. If your ubuntu server has ipv6 enabled, ensure that ufw is configured to support ipv6 so that it will manage firewall rules for ipv6 in addition to ipv4.
The output is either running or not running. How to configure a firewall on linux with firewalld check the firewalld configuration. When a rule is added or modified, by default, only the currently running.
Let us assume that we need to create a new zone called enable_test. To do this, we use the following command: By default, if firewalld is enabled and running and in the public zone, all incoming traffic is rejected.
W elcome to the comprehensive guide to linux firewall using iptables! The firewall rules decide which traffic to. In the realm of linux security, iptables stands as a powerful tool for configuring packet.











/security-2168233_1920-5c5f396246e0fb0001105fb1.jpg)


